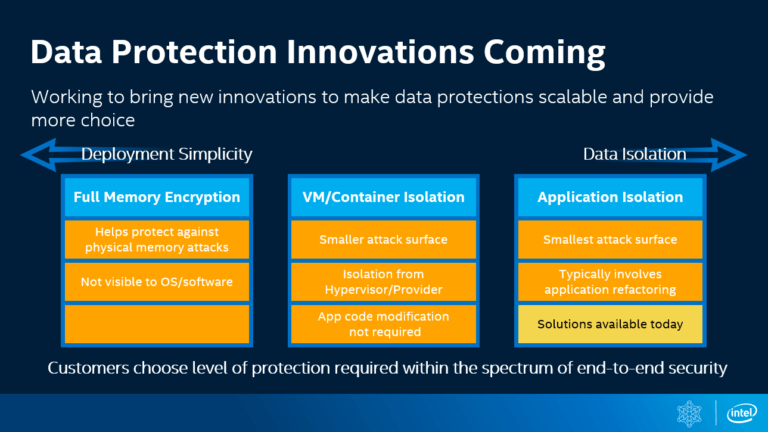
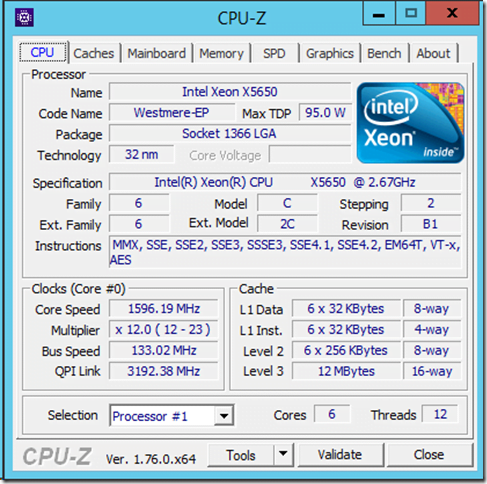
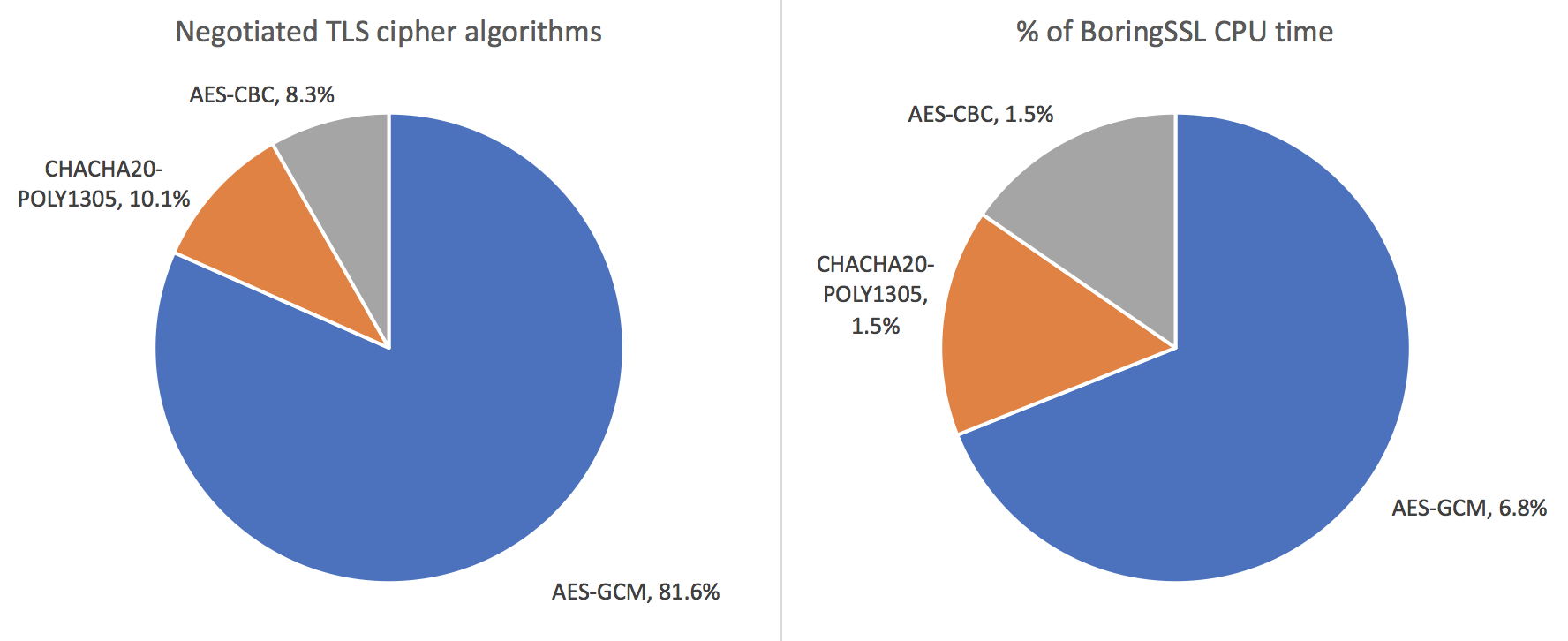
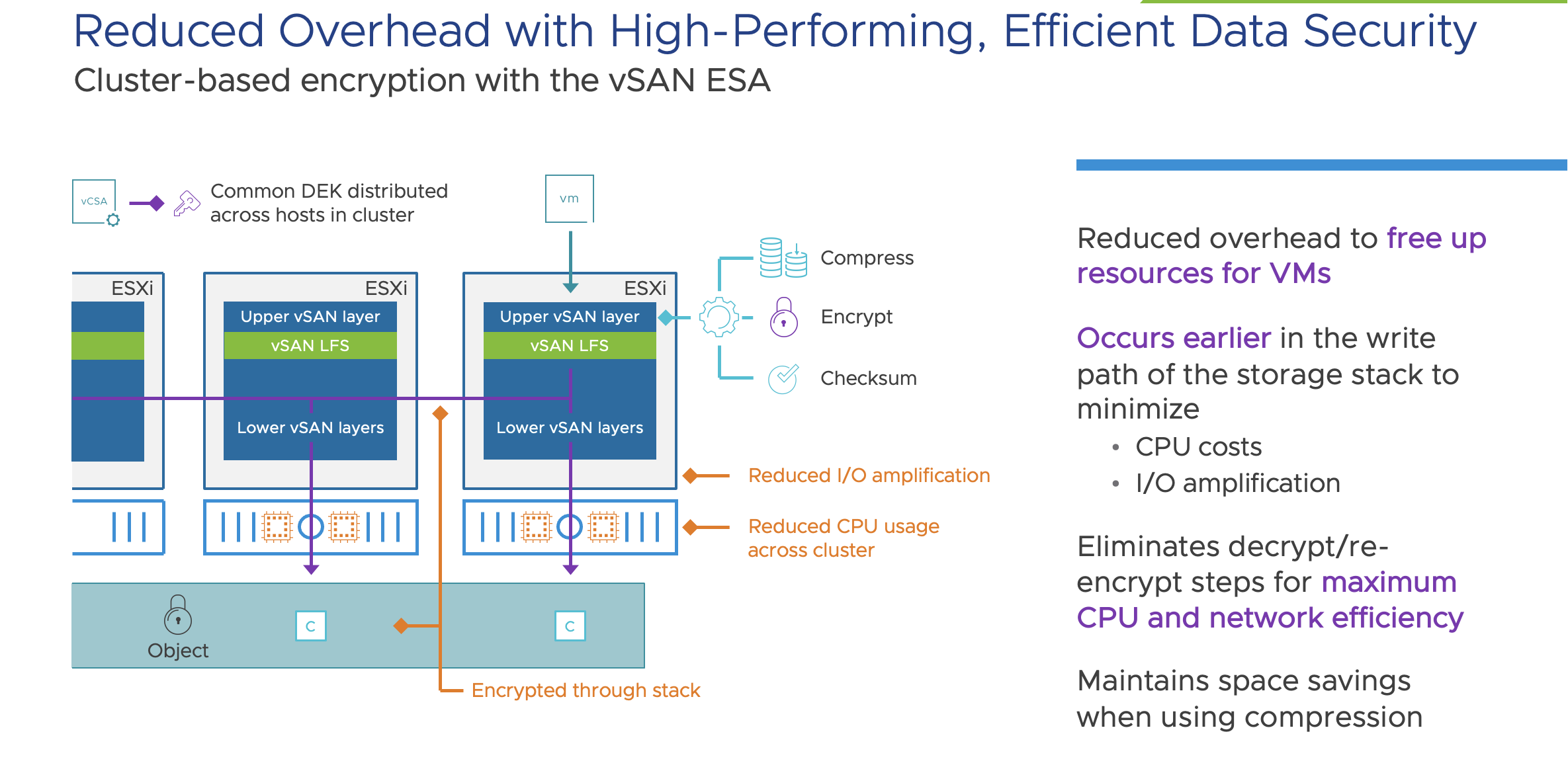
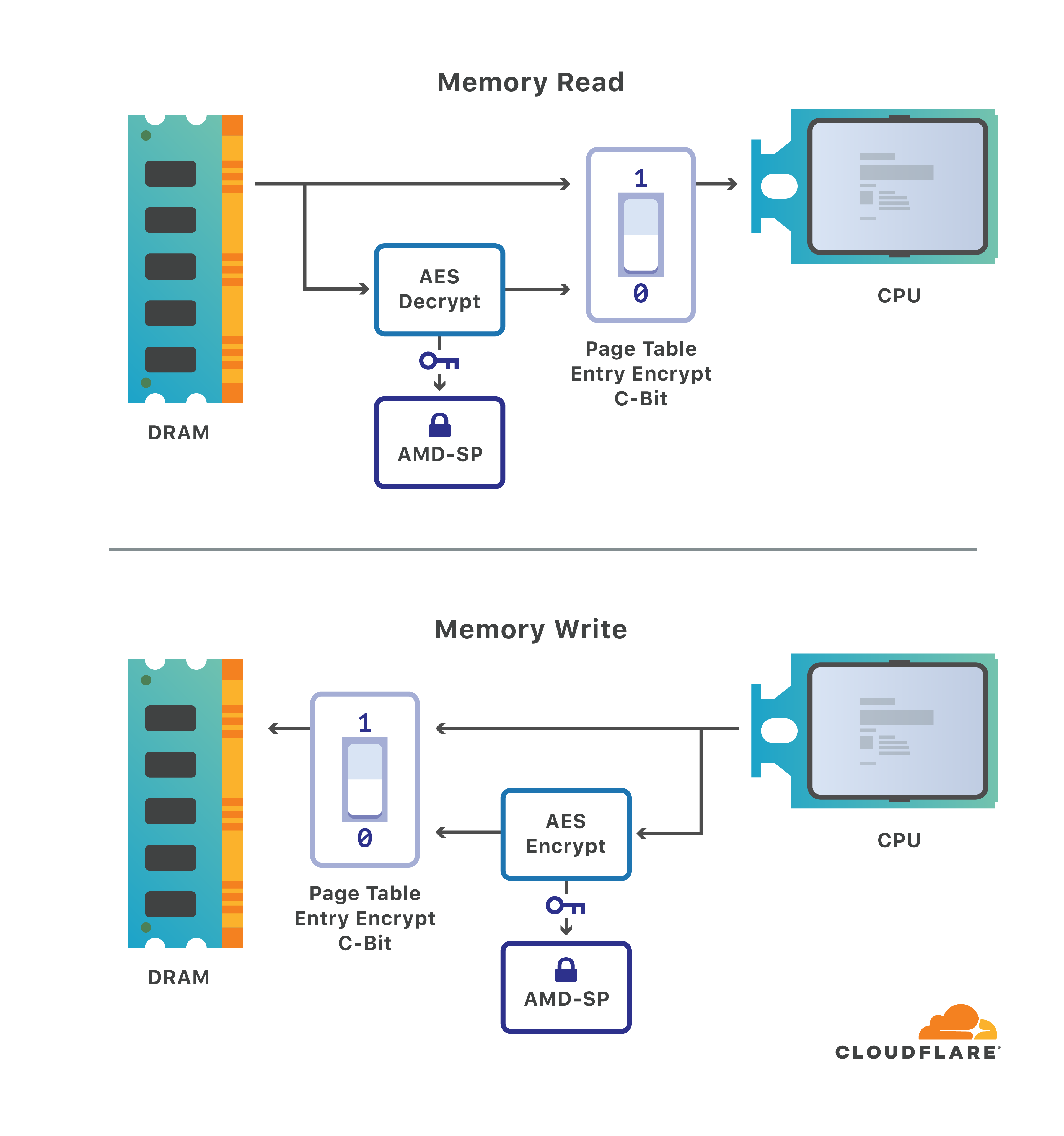
Is encryption in RTI Connext DDS Secure hardware-accelerated? | Data Distribution Service (DDS) Community RTI Connext Users

Researchers crack the world's toughest encryption by listening to the tiny sounds made by your computer's CPU | Extremetech

Windows 11 encryption standard discovered to damage data, fix affects CPU performance - NotebookCheck.net News

What piece of hardware on a computer's motherboard generates encryption keys and only releases a part of the key so that decrypting a disk on a new piece of hardware is not

Comparison of encryption algorithms based on CPU utilization ratio 734 | Download Scientific Diagram

Unfixable" Intel Chip Vulnerability Could Undermine Encryption on Five Years Worth of Computers, But Is a Difficult Attack to Pull Off - CPO Magazine